What is intrinsic security, and how does it impact the future of cybersecurity in the enterprise? Expert Tom Corn guides viewers through the fresh approach.
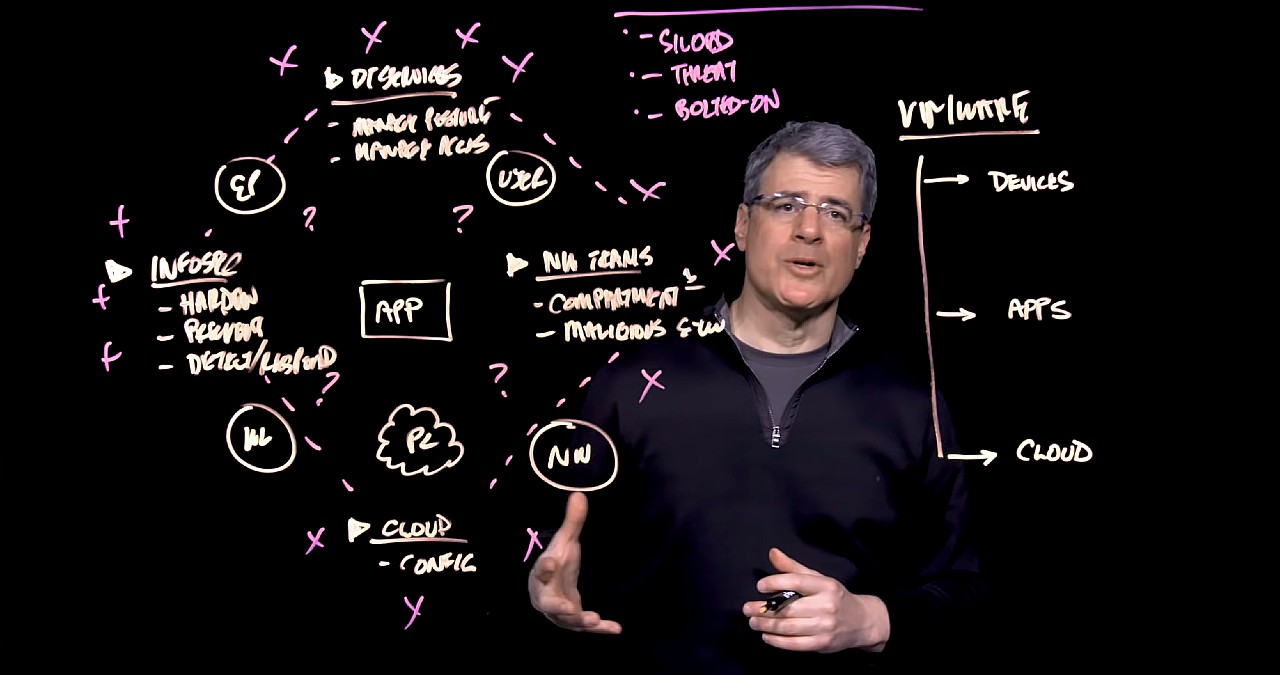
This shift—from siloed to unified, from threat-centric to context-centric, from bolted-on to built-in—allows us to fundamentally transform security.
Tom Corn, Senior Vice President, Security Products, VMware
“Security is a topic playing out in boardrooms all over the world,” says Tom Corn, senior vice president of VMware security products. “It is one of the hottest topics and most serious issues facing organizations the world over.”
Corn says complexity is a fundamental challenge to transforming enterprise security. Applications and data connect to a variety of endpoints and workloads accessed by users across the enterprise network and in the public cloud.
Enterprise teams are evolving in complexity, as well.
- Information security (InfoSec) teams harden endpoints and workloads to prevent, detect and respond to attacks.
- Desktop services teams manage device posture and user access based on trust.
- Networking teams minimize the attack surface and monitor malicious traffic.
- Cloud computing teams securely configure the public cloud elements supporting applications and data.
Unfortunately, he continues, too often the result is:
- Siloed: Each team uses their own set of tools and their own source of truth. They manage each element of app and data security with multiple, siloed technologies.
- Threat-Centric: Security strategies deal more with responding to threats than preventing threats. That’s because these teams and technologies don’t have context and visibility into the overall app infrastructure.
- Bolted-on: Security teams are brought in in the end, not at the beginning of new application builds. Instead of building the infrastructure to support a roadmap, they must bolt on tools and agents for every new app. Misconfiguration and misalignment are huge problems.
The intrinsic security concept turns this traditional approach on its head, Tom explains:
You start with a digital foundation for any app on any cloud on any device, and we leverage the pieces that are already there. Those unique position points that we have to actually understand the application and data from each their own perspective: the network team, the workload infrastructure team, the user device team. They all talk a common language. They all see a common language that are around the application—the thing that we're ultimately trying to protect. The analytics to be able to make sense of that data and the control points in the infrastructure, in the fabric itself, to enforce that policy and, of course, the ecosystem around it.
Intrinsic security is woven into every layer of the digital foundation for any app, any device, any cloud, Corn explains:
- The fabric used to virtualize compute, network and storage.
- The common control plane across clouds.
- The digital workspace for managing device posture and user access.
- The modern application framework used to build, deploy and run apps.
“What that's given us are unique control points with which to understand the application that we’re ultimately trying to protect,” says Corn. “What workloads compose this application? How do they communicate? What network services do they consume? Which users are connecting to those applications? What devices are they using? What is the posture of the devices?”
What was once many different, isolated tools is now a platform for InfoSec, desktop services, networking and cloud teams. As a result, businesses:
- Gain visibility from the cloud to the edge.
- Unify disparate teams and technologies.
- Significantly reduce the attack surface.
- Protect the known good.
“Intrinsic security makes protecting critical applications and data more automated, proactive and pervasive across the entire distributed enterprise” sums up Help Net Security.